Knowing how to password protect an external hard drive is crucial to your overall cybersecurity. ✓ Learn how to protect both PCs and Macs.
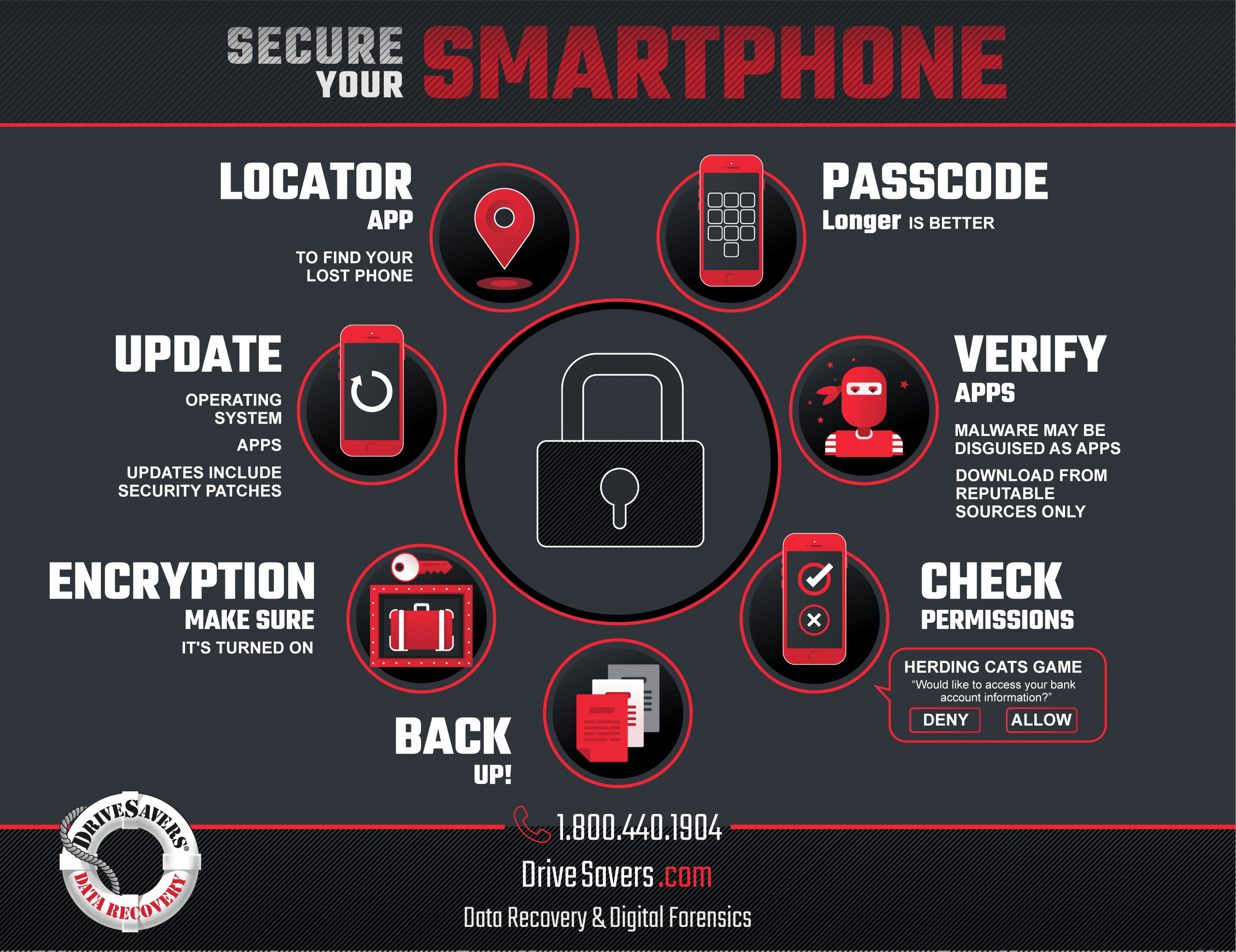
9 Ways to Secure Your Smartphone

By Will DeLisi, NAND Flash Recovery Specialist
Your smartphone–that mini computer that lives in your pocket—deserves the same protection as your personal laptop and work computer does.
Use the following guidelines to protect your on-the-go information from hackers and thieves.
1. Back Up, Back Up, Back Up!
First and foremost, back up your phone regularly. Make multiple copies of important contents—pictures, videos, email, music, documents—and store them in at least two locations, in addition to your phone. Possibilities could be a computer hard drive, an external backup drive or a cloud-based backup service.
Recommended reading: Best Backup Solutions
2. Use a Passcode
Use a passcode or password to protect your smartphone. Do not share the passcode with strangers and do not keep the password on the phone itself. Longer and more complex passwords are recommended.
3. Make Sure Encryption is Turned On
Encryption is becoming a household name, and rightfully so. With the increase of cybercrime comes an increase in the need for cybersecurity.
This tip is really only relevant to Android users since all iPhones and iOS devices ship with hardware encryption built in.
Android phones that ship with Nougat (7.0) and up have hardware encryption enabled by default, so they’re ready to go. However, if you purchased your phone with an earlier operating system (OS), the encryption was disabled by default. With these phones, even upgrading to the current OS will not enable encryption. Instead, it needs to be done manually.
To encrypt your Android device with an OS of Marshmallow (6.0) or earlier, go to Settings > Security > Encrypt Device and follow the prompts. We recommend that you enable encryption before upgrading to anything more current. Once your Android is encrypted, the encryption will remain when you upgrade.
If you purchased your Android phone with an OS of Marshmallow (6.0) or earlier and then upgraded it to Nougat (7.0) or more current, this option will not be located in the Security section of Settings. In this situation, follow the instructions below.
- If your OS is Nougat (7.0) and up, the first thing you should do before following the steps for encryption is BACK UP your phone. The steps to encrypt your Android device include wiping your phone, which will permanently delete all of your data, so be sure to back up you irreplaceable photos, contacts and other data.
- After you have backed up the data on your Android, check your backup to be sure everything you saved is actually there and useable. Sometimes the backup process may get interrupted or otherwise have glitches, so make sure it was completed correctly.
- Go to Settings > About Phone.
- Tap Build Number 7 times. This will enable Developer Options.
- Choose Convert to File Encryption.
- You will be asked to confirm that you want to wipe your device. If you followed steps one and two above, go ahead and confirm. Once the process is complete, encryption will officially be enabled on your Android.
4. Verify Your Apps
Almost any kind of malware can be disguised as a phone app. Users who unwittingly install a fake app can open their entire phone and all the private information it holds to the hackers who created the malware. Personal identity information like social security numbers, geolocation information like home addresses or jogging routes, credit card information and more become available for use by strangers with bad intention. Even common programs like free flashlight apps have been known to hide malware that detects when a banking app snaps a picture of a check, then sends that check image someplace the user did not intend it to go.
Download phone apps from trusted sources only, like the Apple Store and Google Play. Do not put any unsolicited software on your phone. If you come across an advertisement for an app that sounds good to you, do not click the ad to install the app. Instead, go to the Apple Store or Google Play and search for the app there.
5. Check Permissions
Some apps need permission to access personal information and some don’t, so be careful and check the privacy settings for any app before you install it on your device.
Some download requests want blanket access to everything on a user’s system. Users should always review what information the app really needs before downloading anything from any source. Be extremely wary of requests for personal information, like an email account or access to contacts.
In the case of geolocation games and augmented reality games, the app uses your camera and location to play the game. However, if the app were to ask for something that doesn’t make sense or something the user isn’t comfortable allowing, we recommend saying “no” and deleting the app.
6. Keep it Current
Keep your operating system and app software current with the latest updates from the phone manufacturer and app developers. New security measures and improved operating features are included in most updates, which are designed to boost functionality and safety. Security improvements often include patches to gaps in security as they are discovered, so missing an update may expose you to known security loopholes and allow hackers a way to access your personal information.
Before making any changes, make sure your data is backed up.
7. Install a Locator App
Install a locator app that will help you to find your phone if it is misplaced and another app that will allow you to remotely wipe the phone of personal information if it is lost or stolen. Examples include Find My Device in the Google Play store for Android devices and Find My iPhone for iPhones, which generally comes pre-installed. Keep your login information somewhere safe where you can access it in the event that you lose your phone.
If you lose your Android phone, go to android.com/find and log into your Google account.
If you lose your iPhone, go to icloud.com/#find and use your Apple ID to log into your iCloud account.
8. Wifi Security
Ever jump online at a coffee shop or hotel using free public Wifi? It’s risky and here’s why:
A hacker who is connected to the internet through a legitimate wireless access point (WAP) can easily set up a fake WAP that runs through their computer using a software workaround. This fake WAP then shows up as an available free WiFi connection to the unwary victims who think they are using an internet connection.
Anyone who connects to the hacker’s fake WAP runs all of their online data through the hacker’s computer as it goes to and from the real WAP. The hacker now has access to everything being transmitted. That could include online banking transactions, passwords, credit card numbers, vacation plans, home addresses and even more personal information. And that’s just a fraction of the data that could be stolen without victims ever knowing.
Do not use Wifi sources that you are not familiar with. Shut down Wifi and Bluetooth connections when you are done. In addition, make sure your home Wifi is password protected so that outsiders cannot easily access it.
9. Trouble? Power Down.
If an app causes trouble, remove the phone’s battery to stop it from functioning. If the affected phone is an iPhone with a battery that cannot be removed, hold down the Home and Power buttons at the same time until the device turns off. If it’s an iPhone X, press Volume Up, press Volume Down, then hold Power until it turns off.
After powering the phone on again, immediately delete the troublesome app. Often, these malware apps do not show an icon on the home screen, so it may need to be found in settings and deleted from that location.
If the harmful app cannot be deleted, a factory reset may be necessary. Hopefully, the phone will have been backed up prior to the reset. We advise regular backup strategies for important data in case of malware, damage to a device or other data loss situations.
Keep it Up!
Cybercrime is on the rise. With the increase of this type of criminal activity comes an increase in the need for cybersecurity. Now that you know how to secure your smartphone, make a recurring calendar reminder that will notify you every few months and remind you to follow many of the recommendations above. Measures like checking to be sure your operating system and apps are updated and your data are backed up can save you a lot of headaches if ever your smartphone becomes a target.