Don’t Get Caught by Email Phishing Attacks

By Chris Rosa, IT Guru
A lot of smart people are fooled every day by something that looks genuine. Phishing and malware attacks are designed to take something important from you and profit from the theft. This type of attack is directed at individuals and businesses alike. Keep reading to find out what phishing is and how to protect yourself and your business from phishing attempts.
Last year, Google conducted a study examining how passwords are stolen and user accounts become hijacked by hackers. The researchers found that phishing scams posed the greatest threat to users:
By ranking the relative risk to users, we found that phishing posed the greatest threat, followed by keyloggers, and finally third-party breaches.
Interestingly, third-party breaches often originate with phishing emails as well. The third party or contractor is infected and information is gathered about that company’s clients. That information is then used to reproduce the same scam on the newly gathered emails.
Phishing affects personal email accounts like Gmail and Yahoo email accounts and business accounts alike. When these spoofed emails succeed through business emails, the entire company can become compromised, including employee and customer information. A recent example includes the August Legacy Health breach in which 38,000 patient records were compromised.
What is Phishing?
Protecting yourself from hackers should be simple: Don’t open email from strangers. Be suspicious of any links or attachments from unknown sources.
Here’s the problem: the hacker getting ready to send you a message wants you to think everything is okay and normal. They want you to trust them. So they disguise themselves in a way that gets you to do just that.
The ruse normally starts with an email that looks like it comes from someone you know or from a familiar company. It may even be sent directly from a friend’s email address that has been hacked or even spoofed to appear that it’s from your own address. Inside the message are links that look normal, but are actually a direct line to disaster.
Some spoofs are easy to identify. One example is an email from someone you know that contains a link in the body of the email and short, impersonal text such as, “I thought you might be interested in this link.” Don’t click it! Send a message to your friend asking if they sent this email or simply delete it.
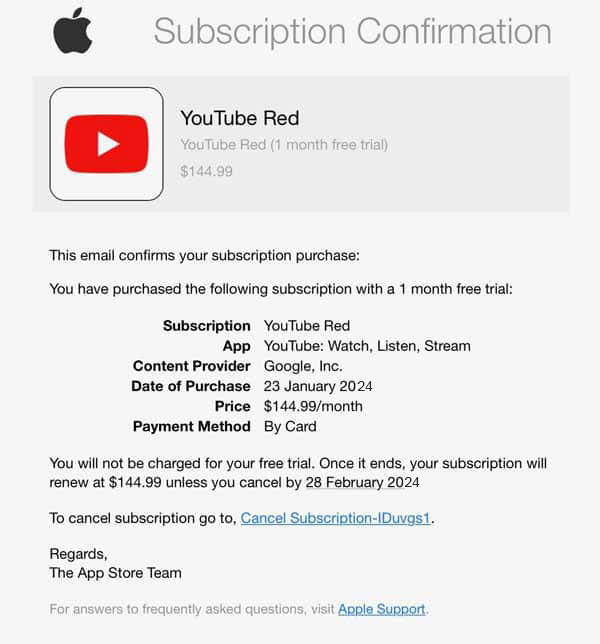
Other scams are far more difficult to recognize. A good example that has become common is the App Store subscription phishing scam. These emails look like legit messages from Apple letting you know that your high priced (sometimes comically so) subscription is confirmed, and offering a cancel button. If you click that, you’ll be taken to a look-a-like Apple site asking for credentials. Don’t be fooled!Other examples of subscription scams include spoofs of antivirus software (like Norton, MacAfee, or Symantec) and GeekSquad subscriptions. These scams may include phone numbers for you to call.
Information Gathering
When gathering your personal information is the goal, there is usually an offer for something of value in return for clicking a link in your email. Clicking this link will then lead to a page disguised as a familiar website, such as Paypal, Google or even your bank. From here, you are tricked into providing valuable information:
- Credit card information
- Bank account information
- Login and password information
- Anything else that might be valuable
Sometimes, the phishing email sent is intended to catch you off guard and frighten you into clicking a link. A common example is an email stating that a child predator has moved into your neighborhood. The end purpose, however, is the same.
You may not even realize this type of attack has happened until hours, days or even weeks later. By then, it may be too late to take any effective counter-action.
Malware
Like the phishing scams above, malware (short for malicious software) attacks are often sent to your email address disguised as a message from a trusted company, coworker or friend. They sometimes include links in the body of the email and sometimes include attachments for you to open or download.
If you click the link or open the attachment, this action will download malware that can open up your computer and its contents to a stranger. The thief may work silently in the background, stealing files and data without your knowledge. Or the attachment you open may download a remote access tool (RAT) that allows the perpetrator complete control of your computer. Sometimes, infiltrators will plant ransomware, a bug that will encrypt the entire drive. The criminals then demand a ransom payment to let you have access to your own files!
Often, this type of attack can spread from one computer to other computers that are attached to the same network. From there, hackers can collect information stored on a coworker’s computer or even the company server.
It Gets Worse
In a study by Wombat Security, 76 percent of organizations interviewed admitted that they had experienced phishing attacks in 2017. When successful, phishing attacks result in malware infections, account compromises and data loss. According to Trend Micro, attacks on businesses are expected to grow by more than $9 billion in 2018.
Other information that could be taken include your address book, which the thieves will use to email your friends and professional contacts (posing as you) and then infiltrate their systems in order to perpetuate the cycle of thievery.
It can be an almost never-ending scenario, unless you protect yourself first with proper security software and some common-sense defensive measures.
Protect Yourself and Your Organization
At the very least, install commercial anti-virus and anti-spam software and keep it current. Have these types of software installed on every computer you or your business uses. You should also use robust Internet security, starting with a strong firewall.
The AV-TEST Institute, an independent testing organization for IT security, does a great job breaking down its findings according to need (business, home user, Mac, Windows, mobile devices, etc.).
Always update and always patch. As software vendors recognize vulnerabilities in their products, updates and patches are developed and distributed. This is probably the easiest security measure you can take: simply turn on automatic updates.
But even the best security software will not protect you from the repercussions of all phishing attacks. The most important thing you can do is educate yourself, your family and your employees on how to recognize and avoid phishing attacks. Here are a few tips:
- Fraudulent links: Hover your mouse over links placed in emails that you receive. This will show you the true address where a link will send you. If the actual hyperlinked address is not the same as the address that is displayed in the email, it is probably fraudulent or malicious. Don’t click the link. Sites like virustotal.com can help you check suspicious URL addresses without subjecting yourself to a hacker.
- Too good to be true: You’ve probably heard of the infamous Nigerian Prince Scam, in which the sender of a message poses as a Nigerian prince who needs your help moving money in return for a large portion of that money. If a stranger is offering money in return for minimal action on your part, or a large chunk of money in return for a small investment, chances are it’s a scam.
- From the government: Government agencies rarely, if ever, initiate contact through electronic methods (email, text or phone). The IRS, for example, ONLY initiates contact through U.S. Postal Service snail mail. If you receive an email from a government agency, it’s likely a scam. Do not reply to the email, click any links or open any attachments. Instead, call the agency and ask about the message. Don’t use any number listed in the email; instead, look up a verified phone number.
- The message asks for account information: If your bank or credit card company is contacting you, they already have your account information and would not request for you to send it to them. This is certainly a scam. If you’re not sure, call the number on the back of your actual bank card or credit card and ask them about the email.
Real-Life Example
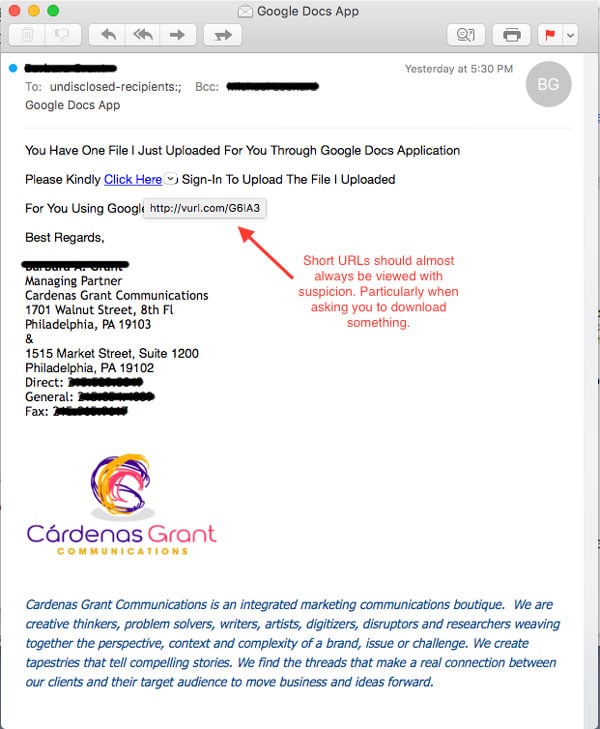
Here’s an example of a suspicious email inquiry sent to a DriveSavers email account.
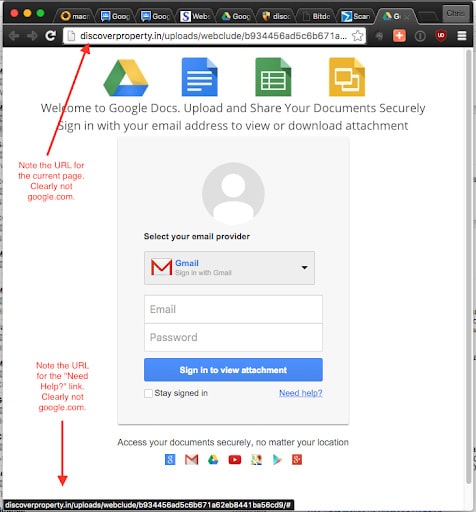
The email contained an Internet link which looked like the regular Google Apps interface. However, hovering the cursor over the suspect link revealed an address for a different location that turned out to be a known malicious site.
Upon investigation of this URL with a few services like virustotal.com, we found that it had a hit as a malicious site.
We investigated further by opening the URL on a secured system. The link directed to a site that was built to look just like that Google Docs login page. One tell-tale sign this was not actually Google Docs, however, was that the URL for the page wasn’t google.com, and none of the links on the page lead to a Google-owned site.
When In Doubt
If in doubt about an email you receive, contact the person listed as the sender to verify with them directly before opening links within the email. If the “sender” did not send the email, definitely do not open any links in the message and delete the email right away.
Another avenue is to simply delete the suspected message and empty the trash. If the sender is bonafide and needs to communicate with you, then they will get back in touch. You may lose some time, but hopefully not your important data!
If you might have been tricked by a phishing email, you can file a report with the Federal Trade Commission at www.ftc.gov/complaint.