Email Security Alert—Messages from Contacts

By Chris Rosa, DriveSavers IT Guru
Be on the lookout for seemingly legitimate messages with attachments.
Known Contact?
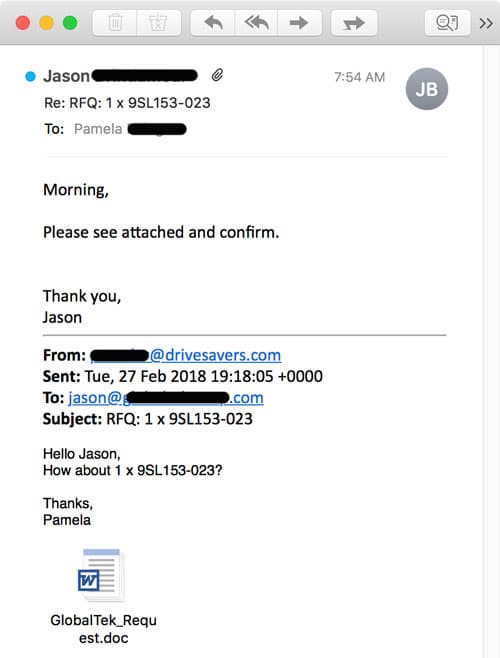
In the real-life example below, Pamela received a reply to a message she had sent to a vendor earlier in the week. In the reply, she is asked to click on an attachment.
As it turns out, the sender, Jason, has a compromised computer. And the virus/malware was actively going through his email and replying to messages with this infected attachment.
If Pamela were to open this Word Doc, it would request for macros to be enabled, etc.
How to Protect Yourself
What can you do to protect yourself from malware that’s actually sent to you from a known contact? Well…it’s tough, to be honest.
This virus is new enough that it wasn’t picked up by any of the server or client-based defenses. The regular preventative measures failed, so it’s up to you to be extra careful with any Microsoft (MS) Office attachments sent to you via email.
For one thing, never enable macros if required to view a document.
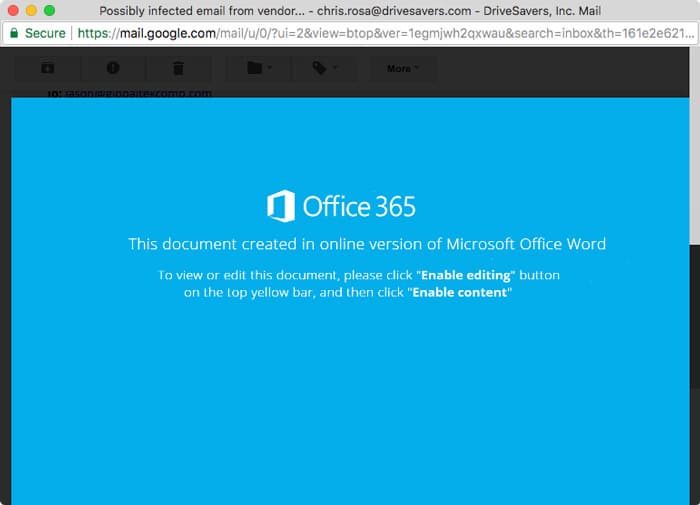
Additionally, it can help to use web-based email like Gmail rather than a native email client, such as Outlook or Apple Mail. Gmail has a built-in attachment viewer so you can check a file out before downloading it. Here’s what that file looks like in that:
How Does Email Become Infected?
How did Jason’s email become infected with this virus that is now sending emails to all of his contacts? Likely in the same manner that Pamela was targeted. Chances are, Jason received a reply to an email he had previously sent to a contact of his and, thinking this was the contact legitimately sending him a document to open, innocently opened the attachment and downloaded the virus.
What’s the Purpose of the Virus?
Clearly, there must be more reason to this virus than simply annoying people with fake emails.
There are many possibilities for why this virus has been created. Once it is opened by a recipient, it will definitely hijack that person’s email and send copies of itself to all contacts it finds there. In addition to that, it may be programmed to do any of the following or more:
- Harvest personal information: collect credit card, bank account, login and password info
- Install ransomware: encrypt the data on a computer and require payment to release the data back to the owner
- Install a remote access terminal (RAT) that the hacker can use to gain control of a victim’s computer
How do You Know if You Have Downloaded a Virus?
The goal, of course, is not to download a virus in the first place. However, as seen in the example above, it’s often difficult to know not to click or open a file. Even after you have opened a malware (virus) attachment, it’s not always obvious that you have downloaded something harmful.
When you click a malware attachment, it will likely ask you to enable macros and may look similar to Pamela’s example above. Any request to enable macros is a fairly certain indication of malware.
Symptoms that you have downloaded something you shouldn’t have may include:
- Your computer is sluggish
- You are blocked from going online
- Your computer might not boot up
- Unknown messages in your sent folder
What to do if Your Computer Becomes Infected
1) Disconnect
Immediately disconnect from any network or other devices, such as wired connections, attached backup drives, printers, shared Wifi or any other possible connections. This is especially important if this happens at work where your computer is connected to the company network!
2) Close All Programs
Closing programs will make it more difficult for a harvesting virus to collect information stored by those programs. Whatever you do, do not enter any usernames or passwords for any reason, as these may be collected and used by the malware.
3) Contact IT or Help Desk
If this is not a company computer, skip this step and go to step 4.
Your company IT or Help Desk personnel will know how to handle a virus problem. If this happens at work, get in touch with them right away (but not by emailing them from the infected computer). Let the professionals take it from here.
4) Back Up
If this is your personal computer and you aren’t ready to go straight to a professional, start by backing up your computer to a new backup drive. Do not back up to a drive that already contains important data, as the virus may migrate from your computer to the peripheral device.
5) Use Antivirus Software
There are lots of antivirus softwares available for download online. Connect your computer to Wifi that is not currently being used by any other devices, do some research for a good option (be sure to read reviews on sites not owned by the software company) and, once you’ve made a choice, purchase and download the software. The antivirus software should come with easy-to-follow directions.
Another option could be downloading software to a different computer and using a USB stick to move it from the uninfected computer to the infected computer. You can also go to a computer store such as Best Buy or Fry’s and purchase antivirus software that can be installed from disk.
6) Time for a Professional
If the antivirus software doesn’t free your computer of the virus, it’s time to call a professional.
Protect Yourself
Always be wary of
- Opening email from someone you don’t know
- Opening unexpected email attachments, even if apparently from someone you do know
- Clicking links
If it looks like it’s coming from someone you know but you weren’t expecting it, just ask. Call them up, text them or send them an email asking if they sent you an attachment or link to open. If they did, they should understand that you are just being cautious. If they didn’t, then it’s a good thing you asked!
Further Reading
Another Crafty Phishing Attack Example
Don’t get Caught by Phishing or Other Email Attacks
6 Ways to Protect Yourself from Hackers